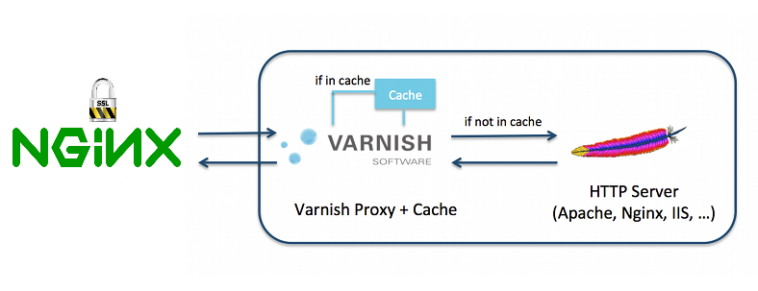
At least 3 reasons, may makes you using Nginx as a reverse proxy
First it can be stand in front of Varnish Cache as SSL Terminal as an alternative solution to Hitch.
“Hitch allow running Varnish behind TLS Layer on the front end side.
Varnish it self does not handle SSL traffic – That’s to keep Varnish in high performance – but just passes all HTTPS traffic straight to Backend.
The Second reason is to used it as Static files Cache Proxy, and the Third one is Gzip for static files too.
In this scenario, as including image Services stands and listen as..
Nginx(Port 80, 443) @ live IP address <=> Varnish (Port 81) @ local IP <=> Apache (Port 8080) @ local IP
Configure Nginx For all missions.
# Redirect http www to https no-www
server {
listen PublicIP:80;
server_name www.mydomain.com;
access_log off;
return 301 https://mydomain.com$request_uri;
}
# Redirect http no-www to https no-www
server {
listen PublicIP:80 default_server;
# listen [::]:80 default_server;
server_name mydomain.com;
access_log off;
return 301 https://$host$request_uri;
}
# Redirect http www to https no-www
server {
listen PublicIP:443 ssl;
server_name www.mydomain.com;
access_log off;
return 301 https://mydomain.com$request_uri;
}
server {
listen PublicIP:443 ssl default_server;
#listen [::]:443 ssl default_server ipv6only=on;
server_name mydomain.com;
# We capture the log, so we can feed it to analysis tools, e.g. Awstats
# This will be more comprehensive than what Apache captures, since Varnish
# will end up removing a lot of the traffic from Apache
#
# Replace this line with: 'access_log off' if logging ties up the disk
access_log /var/log/nginx/access-mydomain.com.log;
ssl on;
# Must contain the a bundle if it is a chained certificate. Order is important.
# cat example.com.crt bundle.crt > example.com.chained.crt
ssl_certificate /opt/ssl.crt/mydomain.com.bundle.crt;
ssl_certificate_key /opt/ssl.crt/mydomain.com.key;
# Test certificate
#ssl_certificate /etc/ssl/certs/ssl-cert-snakeoil.pem;
#ssl_certificate_key /etc/ssl/private/ssl-cert-snakeoil.key;
# Restrict to secure protocols, depending on whether you have visitors
# from older browsers
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
# Restrict ciphers to known secure ones
ssl_ciphers ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256;
ssl_prefer_server_ciphers on;
ssl_ecdh_curve secp384r1;
ssl_stapling on;
ssl_stapling_verify on;
# Caching SSL.
ssl_session_cache shared:SSL:20m;
ssl_session_timeout 180m;
ssl_session_tickets on;
ssl_dhparam /opt/ssl.crt/dhparam.pem;
# Force Users/Visitors Browsers to use security layer.
add_header Strict-Transport-Security "max-age=63072000; includeSubDomains; preload";
add_header X-Frame-Options SAMEORIGIN;
add_header X-Content-Type-Options nosniff;
#New Configuration for Gzip statics.
gzip on;
gzip_static on;
gzip_comp_level 9;
gzip_min_length 256;
gzip_proxied any;
gzip_vary on;
gzip_buffers 16 8k;
gzip_http_version 1.1;
proxy_http_version 1.1;
gzip_types
application/atom+xml
application/javascript
application/x-javascript
application/json
application/ld+json
application/manifest+json
application/rss+xml
application/vnd.geo+json
application/vnd.ms-fontobject
application/x-font-ttf
application/ttf
application/x-ttf
application/font-woff
application/x-font-opentype
application/x-web-app-manifest+json
application/xhtml+xml
application/xml
font/opentype
font/ttf
font/x-woff
image/bmp
image/svg+xml
image/x-icon
text/cache-manifest
text/css
text/javascript
text/plain
text/vcard
text/vnd.rim.location.xloc
text/vtt
text/x-component
text/x-cross-domain-policy;
# text/html is always compressed by gzip module
# To allow POST on static Files
error_page 405 =200 $uri$is_args$args;
location / {
# Pass traffic to Varnish at 127.0.0.1:81.
proxy_pass http://127.0.0.1:81;
proxy_read_timeout 320;
proxy_connect_timeout 320;
proxy_redirect off;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
# Forward Visitor Real-IP in X-Forwarded-For
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto https;
proxy_set_header X-Forwarded-Port 443;
proxy_buffers 8 24k;
proxy_buffer_size 2k;
}
#Caching Static Files.
location ~* \.(jpg|jpeg|png|gif|ico|css|js|pdf|ttf|woff|eot|bz2|gz|woff2|svg|bmp)$ {
# To allow POST on static pages
error_page 405 =200 $uri$is_args$args;
proxy_cache cache;
# Anything that doesn't response with a "HTTP (200|301|302) OK" is not cached.
proxy_cache_valid 200 301 302 1440m;
proxy_cache_key $host$uri$is_args$args;
#This Location Does not inherit the Proxy_Cache configuration so I repeat its confgs.
proxy_pass http://127.0.0.1:81;
proxy_read_timeout 320;
proxy_connect_timeout 320;
proxy_redirect off;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto https;
proxy_set_header X-Forwarded-Port 443;
proxy_buffers 8 24k;
proxy_buffer_size 2k;
access_log off;
log_not_found on;
# Caching at Client/Visitors browsers
expires 60d;
}
}
http {
~~~
# Here we cache requests to /tmp/cache, and we have defined a size-limit on that cache location of 1G
proxy_cache_path /tmp/cache levels=1:2 keys_zone=cache:60m max_size=1G;
~~~
}Referencies
- https://2bits.com/articles/how-configure-varnish-cache-drupal-ssl-termination-using-pound-or-nginx.html
- https://tweaked.io/guide/nginx-proxying/