When Using Reverse Proxy Services Like Cloudflare, you will need to set up your SSL/TLS encryption mode as screenshot shown below.
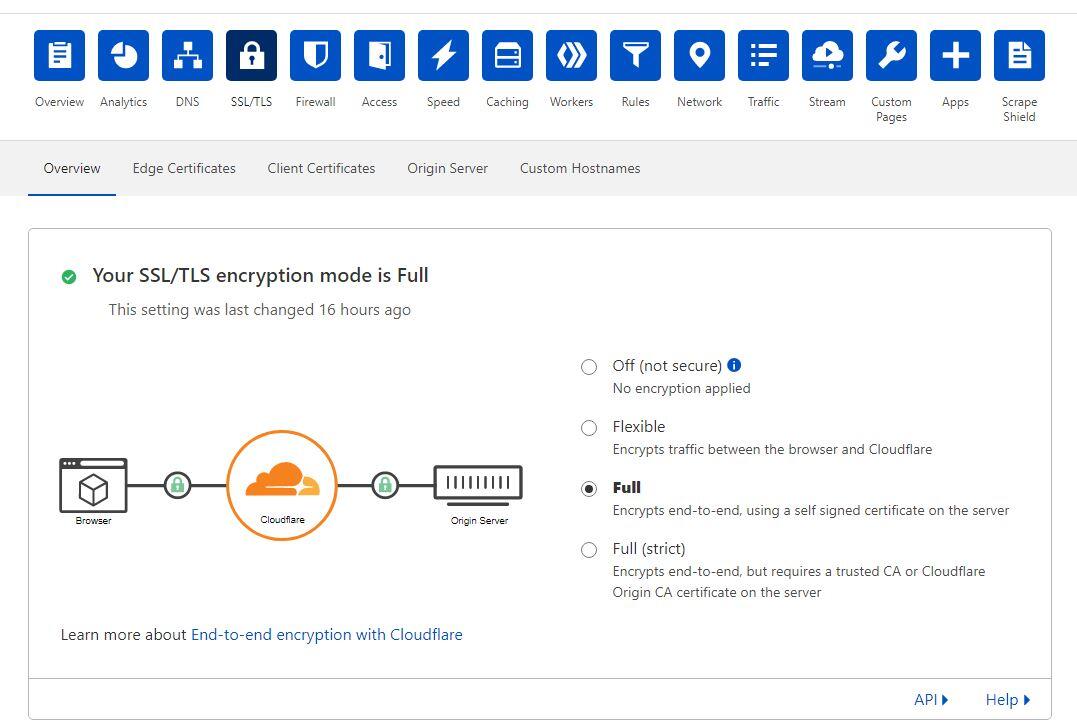
In this article, we will use the Full mode method. and so we will need to create our self-signed SSL Certificate to be attached to the webserver ie Nginx, or Apache servers, and we can do this in the following 3 steps.
In /etc/opt/ directory you can run.
# openssl req -newkey rsa:2048 -new -nodes -x509 -days 13650 -keyout domain.com.key.pem -out domain.com.cert.pem
replace outputs key and cert files name, then fill the default information of your certificate
Generating a RSA private key ......+++++ .+++++ writing new private key to 'netslovers.com.key.pem' ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [AU]:US State or Province Name (full name) [Some-State]:Wyoming Locality Name (eg, city) []:Sheridan Organization Name (eg, company) [Internet Widgits Pty Ltd]:CompanyName Organizational Unit Name (eg, section) []:IT Common Name (e.g. server FQDN or YOUR name) []:domain.com Email Address []:info@domain.com
and for hardening this SSL Certificate we will generate Diffie-Hellman group dhparam.pem file
# openssl dhparam -out dhparam.pem 4096
That’s all, and now we can simply using the output files as our self-signed certificate, for nginx as an example
ssl on; ................... ................... ssl_certificate /opt/domain.com.cert.pem; ssl_certificate_key /opt/domain.com.key.pem; ssl_dhparam /opt/dhparam.pem; ................... ...................



