When browsing the Internet or sending mail when away from your home computer, there is no real way of ensuring it is secure.
However, there is a way of using your VPS’s SSH server as an encrypted SOCKS Proxy – this will ensure your privacy.
Introduction
A SOCKS Proxy is a server that explicitly intercepts client connections, bypassing the default routes and firewall rules of the local network.
There are many reasons why one might want to tunnel their network traffic through a SOCKS Proxy. Here I will go over a few of those reasons and give examples of how to attain this goal.
Benefits
Let’s start off by going over some of the benefits. For starters, all traffic is passed over a secure, encrypted SSH tunnel. This means that you can safely browse the web, chat, email (or what have you) safely and securely without having to worry about people snooping in on your active connections. This comes in extremely handy when utilizing insecure wireless connections or unfamiliar networks.
Both the protocol and software are globally acknowledged and supported amongst the technology industry. You can find client and server software for almost any operating system on virtually any platform.
By tunneling traffic through your remote SSH connection, you give yourself access to your entire infrastructure. This essentially eliminates the hassle of having to use SSH Port Forwarding on an application by application basis.
The beauty of it all is that this only requires two things: a SSH server and a SSH client. Since all of our slices come with a SSH server pre-installed, all you will really need to worry about is the client.
Connect
OS X & Linux
Typically, if you are running OS X or Linux, the easiest way to connect will be from a terminal using the OpenSSH client:
ssh -p 30000 -D 8080 demo@123.45.67.890
Note that this is almost identical to a regular SSH session. We just added the -D switch, where 8080 is the TCP port.
Windows
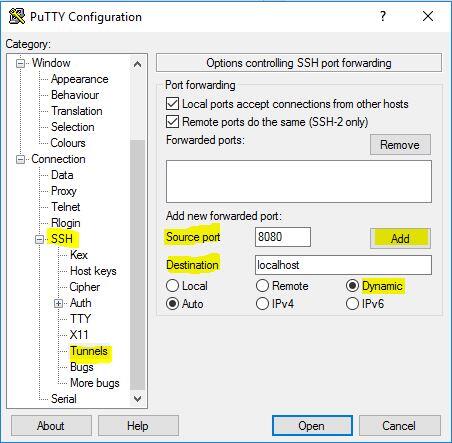
When in Windows I prefer to use PuTTY for a SSH Client. There is an extra step involved in telling PuTTY to create the tunnel. You can see it in the screenshot below:
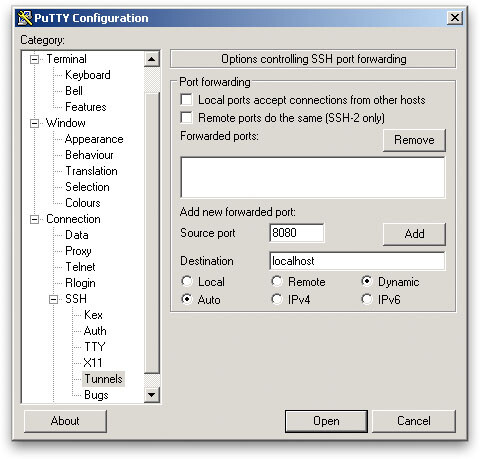
Head into the Tunnels category under SSH. Source port can be anything you’d like; again, I typically use 8080. Destination will always be localhost. Select the Dynamic option then click Add. Proceed to opening the connection.
You can see it in the screenshot below:
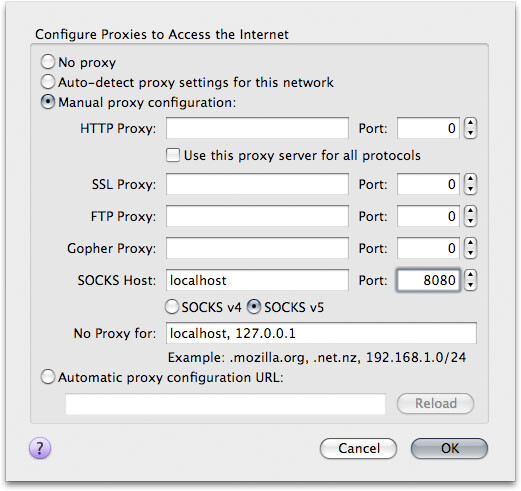
Configure
So now that we are connected, we need to tell our applications to use the secure tunnel. We will use Firefox for our example below. This screenshot was taken in OS X, but you would set the same preference if you were using Linux or Windows:
Summary
Privacy and security are very big concerns for most people these days. This is a great way to achieve both in just few simple steps.
Author: Josh @SliceHost



