Intro
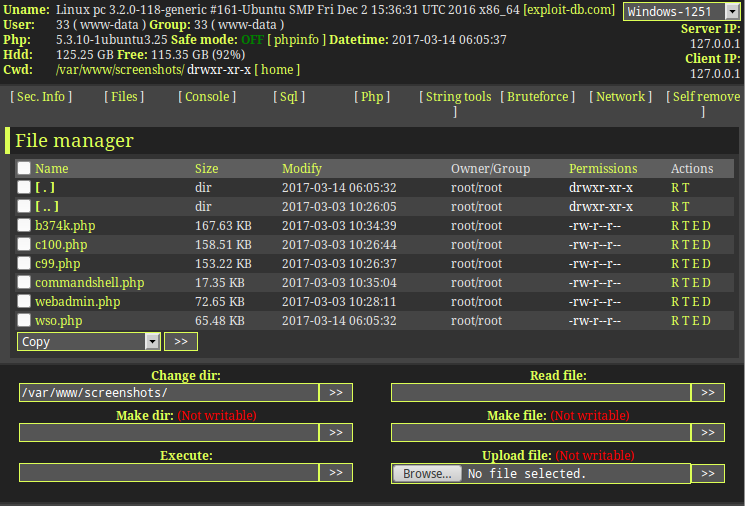
PHP vulnerabilities are the norm, there is not much that can be done to prevent uploads of malicious files on a PHP site when there are world writable directories especially when your website is using a well known opensource community driven software product to power your website.
PHP shell code can usually be found in many websites around the web especially when the administrator does not know much about how to clean out the backdoors after a hack has been done.
Method 01: by Stephen@governmentsecurity:
Here is a simple bash shell script that will search your public_html (DocomentRoot) directories for common file names as well as search all files for common methods used for shell scripts using the fastest possible method with a large number of files. It will dump the results to a file called “php_backdoors” which you can examine to determine what is and what is not a false positive.
To use this shell script just paste this into a file called checker.sh (and gives it an excustion permission #chmod +x checker.sh) in the directory before your public_html folder, then run it with the
following command:
sh checker.sh
#!/bin/bash cd public_html/ find . -type f \( -iname "1.*" -o -iname "sh.php" \) -print0 >> ../php_backdoors find . -type f \( -iname "*.php" -o -iname "*.inc" \) -print0 | xargs -0 -r grep -REn \ '(c99|r57|exif_read_data|extract|passthru|shell_exec|base64_decode|fopen|fclose|eval|Refresh|refresh|justrulz)' >> ../php_backdoors
Method 02: by andrej@Metasploit Notepad
Becuase of Backdoor scripts often need to use PHP commands that most legitimate scripts don’t, so you can search the files in your site for those commands. There are search utility programs you can use
for finding text in files:
- passthru
- shell_exec
- system
- phpinfo
- base64_decode
- edoced_46esab
- chmod
- mkdir
- „ (backticks with an operating system command between them)
- fopen
- fclose
- readfile
On a Linux server, the grep program is already installed as part of the operating system. The only problem is figuring out how to launch it.
If you have command line access to your server (SSH), there’s no problem. You can run it from the command line and have the results displayed to you.
Sample text searches for suspicious PHP code.
Do the search once for each of the suggested PHP keywords listed above.
grep -Rn "mkdir *(" public_html/
OR
grep -RPn "(passthru|shell_exec|system|phpinfo|base64_decode|chmod|mkdir|fopen|fclose|readfile) *\(" public_html/
Method 03: Using PHP Shell Scanner by k2patel@Daily Linux/Unix
#!/usr/bin/perl -w
# findshell v1.0 == code taken/modified from traps.darkmindz.com
#usage: ./findshell.pl
use strict;
use File::Find;
my $sens = shift || 10;
my $folder = shift || './';
find(\&backdoor, "$folder");
sub backdoor {
if ((/\.(php|txt)/)){
open (my $IN,"<$_") || die "can not open datei $File::Find::name: $!";
my @file = <$IN>;
#maybe evil stuffs
my $score = grep (/function_exists\(|phpinfo\(|safe_?mode|shell_exec\(|popen\(|passthru\(|system\(|myshellexec\(|exec\(|getpwuid\(|getgrgid \(|fileperms\(/i,@file);
#probably evil stuffs
my $tempscore = grep(/\`$\_(post|request|get).{0,20}\`|(include|require|eval|system|passthru|shell_exec).{0,10}$\_(post|request|get)|eval.{0,10}base64_decode|back_connect|backdoor|r57|PHPJackal|PhpSpy|GiX|Fx29SheLL|w4ck1ng|milw0rm|PhpShell|k1r4|FeeLCoMz|FaTaLisTiCz|Ve_cENxShell|UnixOn|C99madShell|Spamfordz|Locus7s|c100|c99|x2300|cgitelnet|webadmin|cybershell|STUNSHELL|Pr!v8|PHPShell|KaMeLeOn|S4T|oRb|tryag|sniper|noexecshell|\/etc\/passwd|revengans/i, @file);
$score += 50 * $tempscore;
print "$score - Possible backdoor : $File::Find::name\n" if ($score > $sens-1 );
close $IN;
}elsif((/\.(jpg|jpeg|gif|png|tar|zip|gz|rar|pdf)/)){
open (my $IN,"<$_") || (print "can not open datei $File::Find::name: $!" && next);
print "5000 - Possible backdoor (php in non-php file): $File::Find::name\n" if grep /(\<\?php|include(\ |\())/i, <$IN>;
close $IN;
}
Usage
perl findshell.pl 10 /srv/www/htdocs > scanout.txt sort scanout.txt
GOT MEMORY LIMIT USE FOLLOWING
for i in /srv/www/htdocs/ ; do perl findshell.pl 10 $i >> scanout.txt ; done